Software piracy is the result of products being too expensive for some users, insufficient quality of the software, or a lack of added value between a pirated product and one purchased legally. It is therefore essential to offer impeccable service, an attractive image, regular updates and responsive customer service to ensure absolute customer confidence.
Of course, this is not always enough. For maximum product protection, two steps must be taken:
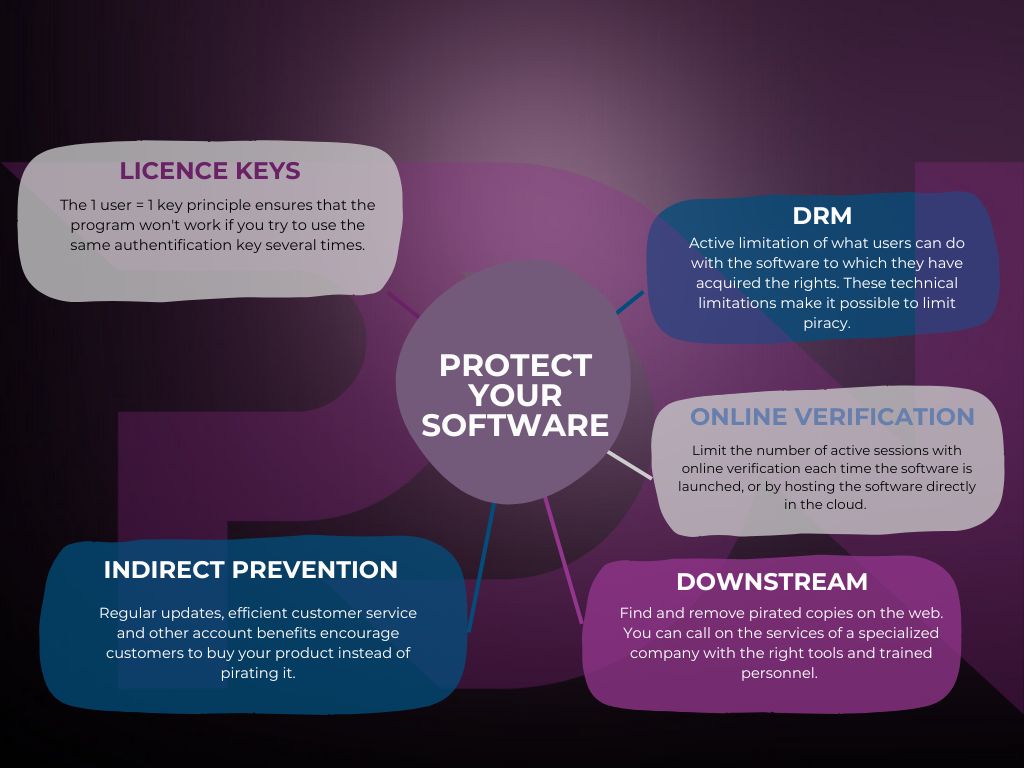
Upstream
- Security measures that protect your software against copying, sharing or redistribution.
- Indirect prevention measures that give your target group additional incentives to buy your product instead of pirating it.If updates are regular and significant, and the publisher listens to feedback from its community, users will often prefer to buy the licensed product rather than pirate it.
Downstream : search and remove illegal copies
A specialized company will search for and remove pirated copies of your products, to make illegal versions of your software hard to find.
If your software is already on pirate direct download and torrenting sites, it will also start appearing in search engine results pages at some point. A specialized company will remove these copies from the sites themselves, and clean up search engine results making the illegal versions much harder to find.
Classic protection measures to fight against piracy.
Licenses, or product keys, are a unique identifier that the user gets when they purchase the right to use your software.
As the program can only function with the license key attached to it, or with the user account, it cannot be copied or redistributed. However, key generators are often available for the most popular programs, enabling you to bypass this barrier.
- Use digital rights management (DRM)
The software you create belongs to you, and user only pays for the right to use it. They’re not buying a physical product.
Digital Rights Management (DRM) is one way of enforcing this rule, but it is often contested by end-users. However, DRM is perhaps copyright protection in its purest form. It can be applied to video games, video and audio files, e-mails, e-books, films and so on. It actively limits how users are allowed to interact with the software or file.
For example, an e-mail can be read, but not forwarded. Even a non-multiplayer video game may require an online connection or verification through an online account.
Proponents of DRMs claim that it is an ideal method of copyright protection, as it limits the use of the software product exclusively to the registered end-user. Opponents, on the other hand, claim that this method limits way too much what the end user who has paid for the rights can do with the product.
- Requiring online verification for software use
This method has also been widely criticized.
It may involve online verification every time the software is used, or the software itself may be accessible from the cloud. An online key, linked to the user’s account will then be a means of accessing the program, often on multiple devices, but limiting active sessions to one at a time.
In conclusion, as in many sectors, the only solution lies in a combination of several methods: looking for the presence of illegal copies online on specialized piracy sites, increased awareness of the consequences of software piracy, and cooperation between companies, governments and users.