Blockchain is often presented as a revolutionary technology, a synonym of security, transparency and decentralisation. Initially used to support cryptocurrency transactions, such as Bitcoin, blockchain has since extended its scope to a variety of fields, including finance, logistics, healthcare and even real estate. However, while blockchain represents an asset for data security, it is also attracting the attention of cybercriminals and hackers. Indeed, certain aspects of blockchain, although secure, are being exploited for malicious purposes, which has led to a rise in attacks and associated new forms of hacking and piracy.

Blockchain is based on the principles of transparency, immutability and decentralisation. It enables data to be stored in a decentralised and immutable way, i.e. without the possibility of modifying or deleting it once it has been recorded. Information is stored in the form of ‘blocks’ linked together chronologically to form a chain. The blocks of data are linked together by cryptographic hashes, guaranteeing the integrity of the information recorded. Once a transaction has been validated and added to a block, it cannot be modified or deleted without altering the entire chain, making forgery extremely difficult.
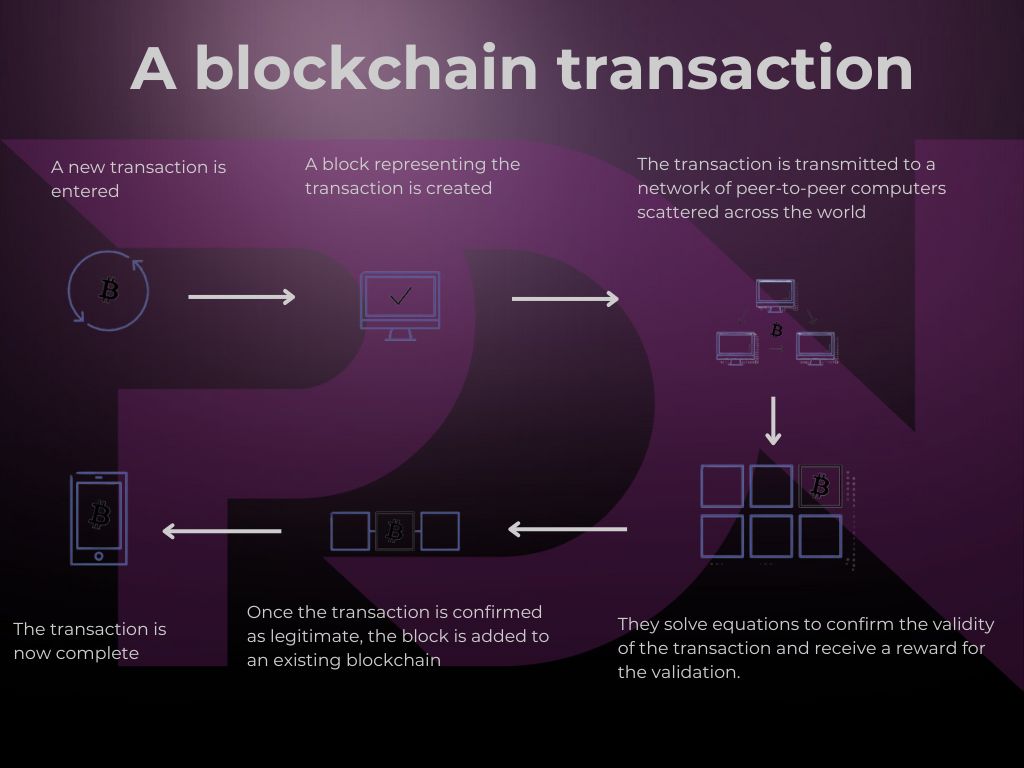
A blockchain is a kind of digital ledger distributed and shared between several users. A blockchain consists of programmes called script, that perform the tasks usually carried out in a database: entering and accessing information, recording it and storing it somewhere. A blockchain is distributed, which means that several copies are stored on many machines and they all have to match to be valid. The data are identified as follows:
Transaction data (or other information depending on usage)
A timestamp to indicate when the data was added
A unique identifier in the form of a ‘hash’ to ensure data integrity and security.
Public blockchain networks
Public blockchains require no permission and allow anyone to join. All members of the blockchain have the same rights to read, edit and validate d. People mainly use public blockchains to trade and mine cryptocurrencies such as Bitcoin, Ethereum and Litecoin.
Private blockchain networks
A single organisation controls private blockchains, also known as managed blockchains. It determines who can be a member and what rights they have within the network. Private blockchains are only partially decentralised because they have access restrictions. Ripple, a digital currency exchange network for businesses, is an example of a private blockchain.
Hybrid blockchain networks
Hybrid blockchains combine elements of both private and public networks. Companies can set up private, permission-based systems alongside a public system. In this way, they control access to specific data stored in the blockchain while keeping the rest of the data public. They use smart contracts to allow public members to check whether private transactions have been carried out. For example, hybrid blockchains can allow public access to digital currency while keeping bank-owned currency private.
Consortium blockchain networks
A group of organisations governs consortium blockchain networks. The pre-selected organisations share responsibility for maintaining the blockchain and determining access rights to the data. Sectors in which many organisations have common goals and benefit from shared responsibility often prefer consortium blockchain networks. For example, the Global Shipping Business Network Consortium is a not-for-profit blockchain consortium that aims to digitise the shipping industry and increase collaboration between shipping industry operators.
The main advantages of blockchain are :
Check back in mid-November for the second part of our article. We’ll be looking at how blockchain can influence both piracy and anti-piracy measures. In the meantime, if you have a film, series, software or e-book to protect, don’t hesitate to call on our services by contacting one of our account managers; PDN has been a pioneer in cybersecurity and anti-piracy for over ten years, and we’re bound to have a solution to help you. Happy reading and see you soon!
Share this article