Despite technological advancements and massive investments in cybersecurity solutions, security breaches continue to occur. The main reason for this is that one of the most vulnerable elements in this field remains the human factor: user errors, negligence, and social engineering are just a few of the factors that make average digital users responsible for many security breaches. This month, we will explore why humans are often seen as the weakest link in cybersecurity and how this vulnerability can be mitigated.
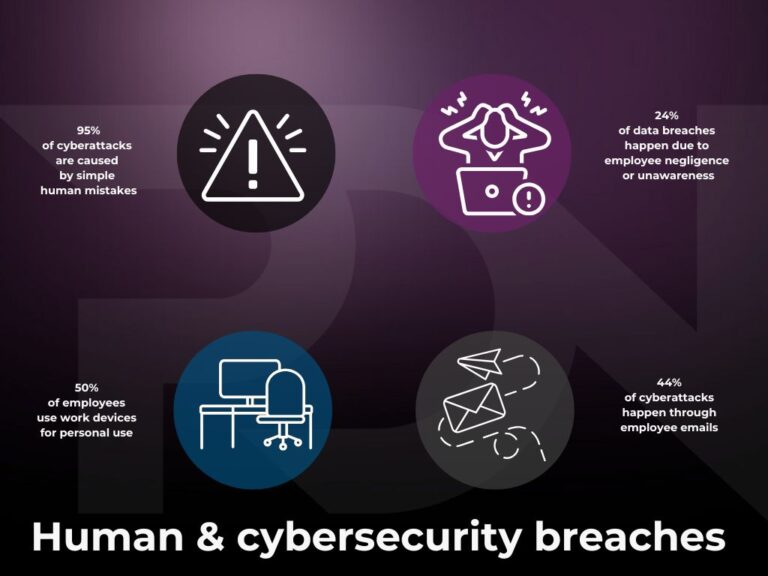
Human error is one of the leading causes of cybersecurity incidents. According to numerous studies, between 80% and 95% of successful cyberattacks exploit human vulnerabilities rather than technical ones.
Many users fail to grasp the full extent of the risks posed by cyberattacks. A weak password, connecting to an unsecured public Wi-Fi, or neglecting security updates are all behaviors that compromise system safety, even though the user has no malicious intent.

Employees often bypass their company’s cybersecurity rules, either out of convenience or due to a lack of resources. The use of unapproved software or unsecured personal devices is a common practice that exposes businesses to significant risks.
Shadow IT refers to all tools, software, and services used without the approval of an organization’s IT department: using unsecure online storage platforms, public messaging apps, or unapproved collaborative tools. These practices, often driven by a desire for productivity and flexibility, introduce significant security vulnerabilities.
To mitigate the impact of Shadow IT, it is crucial to educate employees about the risks it poses, establish clear control policies, and provide secure alternatives that meet the needs of employees.
Cybercriminals exploit human psychology to obtain confidential information. This approach, known as social engineering, is often more effective than purely technical attacks.
Phishing remains one of the most common attack methods. It involves deceiving users into believing they are interacting with a trusted organization (such as a bank, government agency, or company) in order to steal sensitive information.
Among the variations of phishing are:
Cybercriminals know how to manipulate human psychology to control their victims. Some commonly used techniques include:
Fear: Alarmist messages (such as fake security alerts or threats of account closure) prompt users to act without thinking.
Urgency: Time-limited offers or demands for immediate action push victims to provide information without verifying its authenticity.
Curiosity: A fake document, an intriguing video, or a supposedly confidential file may contain malware.
Authority: Cybercriminals impersonate authoritative figures (such as CEOs, technical support, or government agencies) to intimidate their targets and extract sensitive information.
Social engineering also relies on elaborate scenarios to manipulate victims. Some of the most commonly used techniques include:
Join us in mid-March for the continuation of our article. In the meantime, if you have a movie, series, software, or e-book to protect, don’t hesitate to reach out to one of our account managers. PDN has been a pioneer in cybersecurity and anti-piracy for over ten years, and we definitely have a solution to assist you. Happy reading, and see you soon!
Share this article