At the outset, crypto-currencies were the stuff of dreams: an autonomous financial system, free from banks, states and borders. More transparency, more freedom, more privacy. Fifteen years after the emergence of Bitcoin, these promises are still there, but the picture is much darker. For what promised to be a revolution for the world’s citizens has also become the weapon of choice for modern cybercrime. Ransomware, scams, money laundering: crypto-assets are now at the heart of the financial mechanics of the majority of computer attacks.
So it’s essential to understand how they work, what they’re used for, and where the grey areas lie. In this first part, we’ll look at why crypto-currencies are so attractive to cybercriminals, what mechanisms are used, and where the real risks lie for businesses.
Contrary to popular belief, crypto-currencies are not totally anonymous. On most blockchains (such as Bitcoin or Ethereum), transactions are public, visible to all, and stored indefinitely. But this does not mean they are identifiable. Each transaction is linked to a cryptographic address, not a real identity. And therein lies the problem: this pseudonymity leaves the field wide open to cybercriminals, who use tools to further muddy the waters – mixers, tumblers, conversions between currencies or even proxy purchases.
In 2023, according to Chainalysis, over $24 billion in crypto-assets were identified as linked to criminal activity.
More often than not, these funds pass through anonymous wallets, then offshore platforms before being laundered into the real economy. And both security teams and law enforcement agencies then have to work their way up complex and deliberately opaque chains.
Crypto combines several key advantages that are highly attractive:
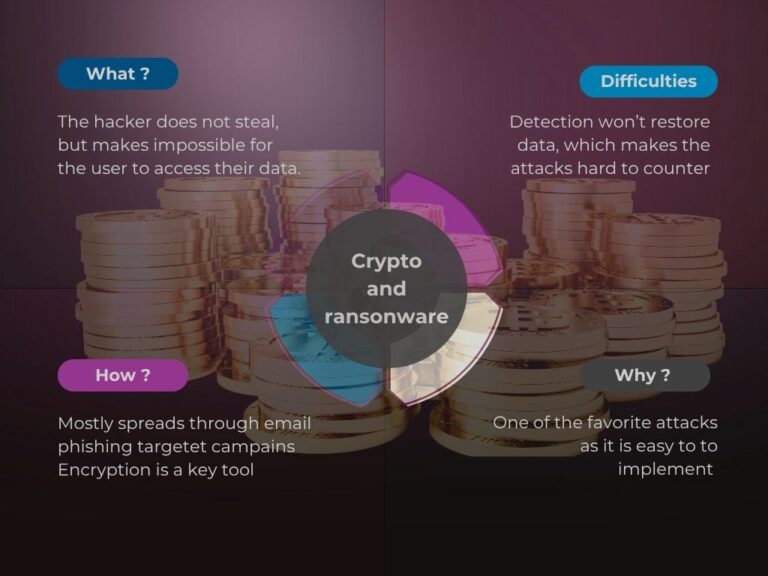
Where crypto-currencies really become a problem for businesses is in their use as extortion currency. Ransomware attacks have exploded in recent years, affecting hospitals, local authorities, SMEs and multinationals alike. Today, ransomware groups almost systematically demand ransoms in Bitcoin or Monero. The modus operandi is now well-honed: attack, data encryption, ransom note with QR code for payment, then threat of disclosure.
Crypto is ideal for these attacks because it ticks all the boxes:
With the rise of “double extortion” – encryption under threat of publication of sensitive data – companies are faced with a dilemma: pay and risk breaking the law, or refuse and see their data exposed.
This is not just a technical issue. It’s also a major legal issue. When a company falls victim to ransomware, it almost systematically enters the red zone with regard to data protection regulations.
The General Data Protection Regulation (GDPR) imposes a notification obligation in the event of leakage or unauthorized access to personal data. In the event of double extortion, a company that pays without reporting faces penalties of up to 4% of its worldwide sales.
In the United States, there are several pieces of legislation, depending on the state. The most advanced is the California Consumer Privacy Act (CCPA), which imposes obligations similar to those of the RGPD for companies operating in California.
In Canada, the Personal Information Protection and Electronic Documents Act (PIPEDA) governs the management of personal data, and also imposes transparency obligations in the event of a breach.
In all cases, regulators are clear: paying a ransom does not exonerate you from your responsibilities in terms of security and confidentiality. And in some countries, payment to sanctioned groups can even be equated with terrorist financing.
In the hands of a cybercriminal, a crypto ransom only has value once it has been converted into real currency. This is where exchange platforms come into play, bridging the gap between the digital world and the conventional financial system.
Regulated platforms, such as Coinbase or Kraken, apply strict KYC (Know Your Customer) procedures. But many smaller exchanges, often based in offshore jurisdictions, are much more lax – if not totally opaque.
Some services even offer built-in anonymization features: automatic change of address, converter to confidential crypto-currencies, etc. And until global regulations are harmonized, these loopholes will continue to be massively exploited.
We sometimes forget it, but crypto platforms are also prime targets for cyberattacks. Theft of funds, ransomware, compromise of customer data… There’s no shortage of examples:
So even when a company chooses to pay a ransom, there’s no guarantee that the funds will arrive safely… or that confidentiality will be preserved.

Crypto-currencies are not inherently bad. They are neutral by nature, and their potential is immense in the fields of finance, traceability, smart contracts…
But their decentralized, pseud-anonymous structure also makes them powerful tools for cybercriminals. And for businesses, this means a new level of vigilance:
In the second part of this article, we’ll explore traceability tools and best practices in the event of an attack. In the meantime, if you have a film, series, software or e-book to protect, don’t hesitate to call on our services by contacting one of our account managers; PDN has been a pioneer in cybersecurity and anti-piracy for over ten years, and we’re bound to have a solution to help you. Enjoy your reading, and see you soon!
Share this article